Category: Security
-
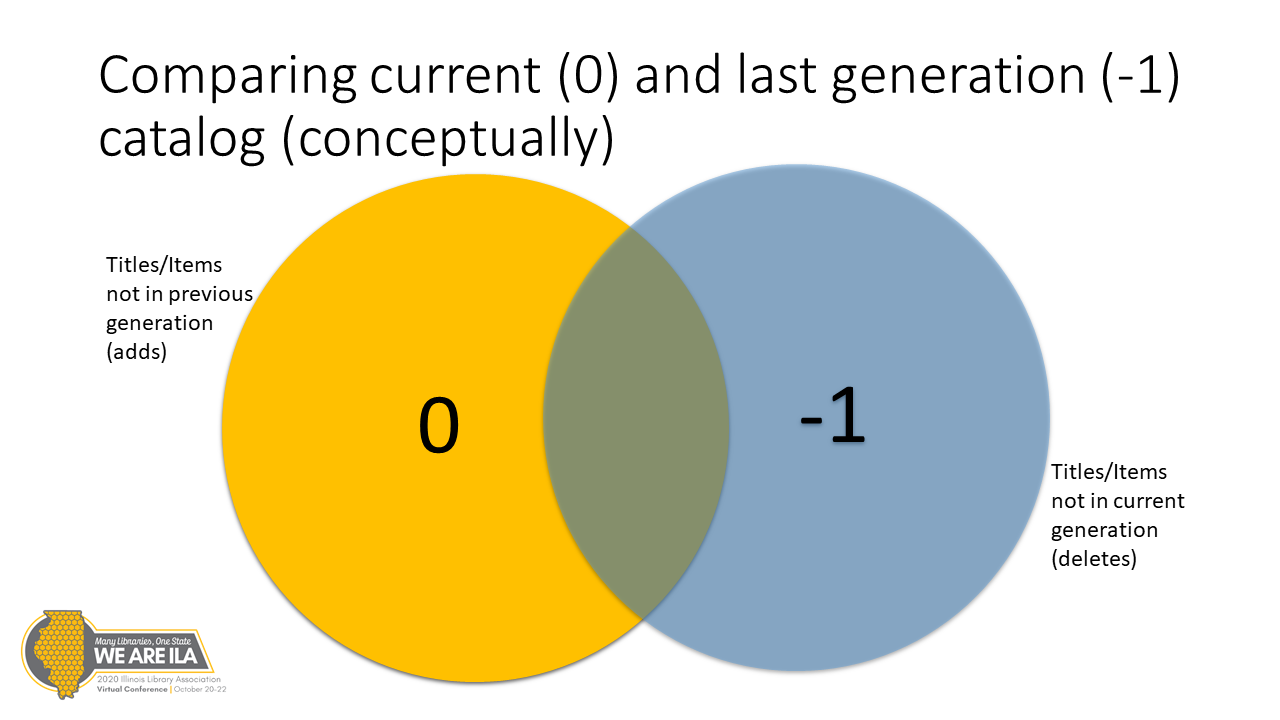
OCLC Holdings Manager: a primer
How the library open-source project OCLC Holdings Manager came about and what it means for libraries.
-
Libraries & Leaky Data, Part 3
Part 1 of this series provided an overview of how library user data ends up in a variety of places within your library other than just the ILS. Part 2 of the series explained how your library services communicate over the network or across the internet in a variety of insecure ways. This is Part…
-
Libraries & Leaky Data, Part 2
In my first post of the series “Libraries & Leaky Data,” I provided an overview of how libraries are accumulating patron information in a variety of “hidden” areas of the library. I noted that if a library were to be subject to a ransomware attack, it is possible that patron information could be stolen from…
-
Libraries & Leaky Data, Part 1
The ILA Best Practices Committee has recently been tasked with studying the issues of patron privacy around the use of printed hold wrappers in public areas. It is good to see a focus on the most obvious aspects of protecting patron’s privacy since having a patron’s full name stuck on a book in a public…